eBPF Simple Firewall with Rust and Aya
eBPF’s Role in Networking and Security
eBPF can create highly efficient and configurable network functions directly within the Linux kernel. It allows developers to program the network packet processing capabilities of the operating system with great precision. This capability includes but is not limited to:
Filtering and analyzing network packets at various points in the network stack. Implementing security policies that are more dynamic and context-aware than traditional firewall rules. Monitoring network traffic in real-time, which can be used for both security and performance optimizations.
Traditional Firewalls vs. eBPF-based Approaches
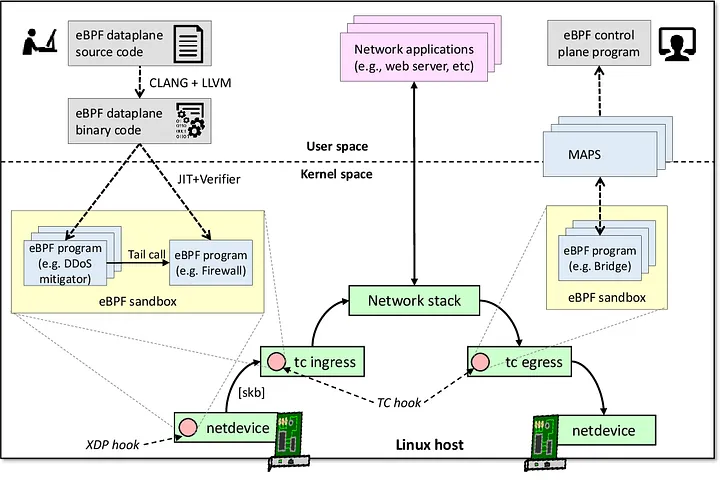
Traditional firewalls (both hardware and software-based) typically operate at specific layers of the network stack, predominantly focusing on filtering and blocking traffic based on a set of predefined rules. Here’s how eBPF compares and contrasts with traditional firewalls:
- Flexibility: Traditional firewalls have static capabilities defined by their hardware and software architectures. eBPF, on the other hand, allows for the dynamic insertion of custom code into the kernel, enabling more adaptive and intelligent behaviours based on real-time data.
- Performance: eBPF runs within the Linux kernel with very low overhead, making it highly efficient for operations like packet filtering and inspection. This can lead to better performance compared to traditional firewalls, especially in environments with high network traffic volumes.
- Functionality: eBPF extends beyond simple packet filtering to include a broader range of functions such as system call filtering, network routing decisions, and complex data gathering for security and monitoring.
Will eBPF Replace Traditional Firewalls?
While eBPF offers many advantages, it’s not likely to completely replace traditional firewalls due to several reasons:
- Comprehensiveness: Traditional firewalls, especially those integrated into broader network security solutions, offer a range of features like VPN management, anti-malware functions, and intrusion prevention systems that are not directly related to what eBPF is designed to handle.
- Ease of Use: Configuring and managing traditional firewalls is generally more straightforward for most users and organizations than developing custom eBPF code. Traditional firewalls come with user-friendly interfaces and support, making them accessible to a broader audience.
- Security and Compliance: Many organizations are subject to regulatory requirements that specify the use of certain types of security measures, including traditional firewalls. These organizations may not see eBPF as a replacement but rather as a complementary technology.
Conclusion
eBPF is an exciting technology that pushes the boundaries of what’s possible within system and network security domains. It complements existing technologies and, in some cases, provides a more flexible and high-performance alternative to traditional approaches.
However, it is part of a broader ecosystem of security tools and is best used in conjunction with other security measures, not necessarily as a replacement for them. The future of network security likely involves a combination of both traditional methods and innovative approaches like eBPF, each playing a role in defending against increasingly sophisticated threats.