Berkeley Packet Filter (BPF) was initially developed in 1992 to filter packets before they were received by the kernel or even worse by the user space; the tool was re-written and included in Linux Kernel in 2014, now named the extended Berkeley Packet Filter (eBPF). eBPF can be conceived as a lightweight, sandboxed virtual machine (VM) within the Linux kernel - eBPF programs are invoked by the kernel when certain events, called hooks, occur. Examples of such hooks include system calls, network events. These processes enable deep analysis into events, and even enable security actions to be performed with low overhead.
In addition to several architectural improvements, eBPF introduces the capability of handling generic event processing in the kernel, JIT compiling for increased performance, stateful processing using maps, and libraries (helpers) to handle more complex tasks, available within the kernel. When a certain event or hook happens, the eBPF application is invoked and run with an extremely low overhead, as there is JIT compiling. eBPF programs can be written in restricted C and compiled using the LLVM Clang compiler, or in eBPF assembly instructions and converted to bytecode using the bpf asm utility. The bytecode can then be loaded using the bpf() system call. A loaded eBPF program follows an event-driven architecture and it is therefore hooked to a particular type of event. Each occurrence of the event will trigger its execution, and, based on the type of event, the program might be able to alter the event context as shown in Fig. 2. In this case, we are able to perform an action if a specific condition is met; these actions are varied - for example, actions may cause events to be logged in a monitoring system, or perform security routines, etc.
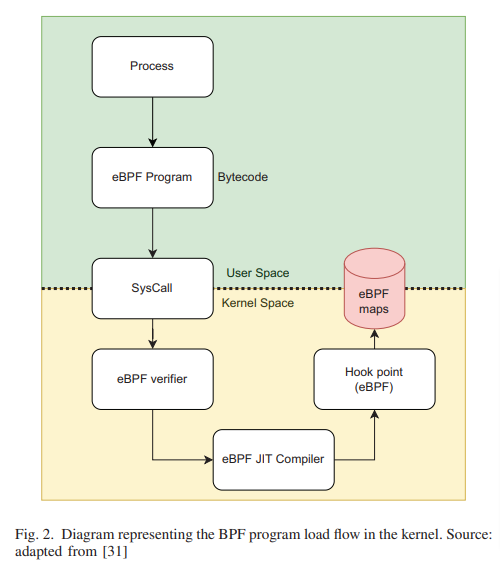
eBPF is a revolutionary technology that allows developers to run sandboxed programs directly within the Linux kernel. Unlike traditional kernel code, eBPF programs are loaded into the kernel at runtime, offering a dynamic way to execute custom logic in response to various events. These programs are written in a restricted subset of C, compiled into eBPF bytecode, and run in a virtual machine-like environment provided by the kernel, ensuring safety and efficiency.
The Origins and Evolution of eBPF
The journey of eBPF began with the Berkeley Packet Filter (BPF), designed for efficient packet filtering. However, the modern eBPF extends far beyond its networking roots. Today, it can attach to almost any point in the kernel, providing unparalleled visibility into the system’s inner workings. This extension was driven by the need for a more programmable, universally applicable tool to meet modern high-performance applications’ demands.
Key Applications of eBPF
BPF’s capabilities make it a great tool across various domains:
- Networking: eBPF excels in network packet processing, enabling the creation of highly customizable network applications directly in the kernel. Tools like XDP (eXpress Data Path) leverage eBPF to process packets at the network driver level, dramatically increasing performance.
- Security: eBPF provides powerful facilities for implementing runtime security monitoring and policy enforcement, such as detecting and preventing unwanted behaviour in applications.
- Observability: Perhaps one of the most powerful uses of eBPF is in observability. It can gather detailed and context-rich system metrics and logs, helping developers pinpoint performance bottlenecks and understand complex system behaviour.
- Tracing and Profiling: eBPF can trace kernel functions and user-space applications with minimal overhead, making it ideal for performance analysis and debugging.
Reference List
- Sedghpour, M. R. S., & Townend, P. (2022, August). Service Mesh and eBPF-Powered Microservices: A Survey and Future Directions. In 2022 IEEE International Conference on Service-Oriented System Engineering (SOSE) (pp. 176-184). IEEE.
- https://www.youtube.com/watch?v=ThtRT8dhu8c&ab_channel=CodingTech
- https://www.tigera.io/learn/guides/ebpf/
- https://www.oreilly.com/library/view/learning-ebpf/9781098135119/ch01.html
- https://mp.weixin.qq.com/s?__biz=MzkyMjM4MTcwOQ==&mid=2247484503&idx=1&sn=017208e9f66a7fd32fea781983e7071b&chksm=c1f478b5f683f1a3e67cc1a18674b8e220e39014b214829a11a533b827160c7fa55a7b008879&mpshare=1&scene=1&srcid=1106ntuRC4alaxcfKeaHM9xE&sharer_shareinfo=5a5190f46ae859e89aa44a20f481dcee&sharer_shareinfo_first=5a5190f46ae859e89aa44a20f481dcee&exportkey=n_ChQIAhIQFaCC9WCNvkGEnvxqNpc0WBKWAgIE97dBBAEAAAAAAJ6yLRyWlqIAAAAOpnltbLcz9gKNyK89dVj0eyuX4vZNXOtab1psjJl8DZbtnzMFalMlMx053haZ%2FVeOsBXHPMyHrX%2BELzJms1NTtbEMcJWDB82RcYgzYfu7GS4QlViiibLhguNscxfk3k3JsbCAMxmGVIx4%2BntuqSBqCWbO6eaKjqxaFaPwtVObh6WBQbeQKkGMWsdKsYSvzk4JxMG6OYwQ7KZxOYZdT0dDk5UlvY2%2FFWWhDdapETg%2BncSSFAimQs8ohdp15sYnMH28%2FeiNTbOqJ2FDAfTd89rAPkp9GwuLThO7qt0fEilBhX%2FzAXcNhx8a5lYpAUCWxZ58k3fivNJPKerNoJ%2FsWsxB&acctmode=0&pass_ticket=E%2BmnNp%2Bw0XZsXNvf0lisNyjUvGGBaKp56bDCQei7wgiLvyHJdhYYv3BQKQ9PsNE3JY4N6SQdTajfHQuR3z66Pg%3D%3D&wx_header=0#rd
- https://mp.weixin.qq.com/s?__biz=Mzg2Mjg0MTU0MQ==&mid=2247485900&idx=1&sn=6c60131c34c29d594b5f8d9468c4f5fd&chksm=ce00f666f9777f706ec8a8b2279a8e2c1f1802cdb12cb0eeccceb22402ae99db3647632c73c6&mpshare=1&scene=1&srcid=1107JdiUudHoifZCw0wjz1ki&sharer_shareinfo=7db2163a00f703d00d2313d8d9f8383c&sharer_shareinfo_first=7db2163a00f703d00d2313d8d9f8383c&exportkey=n_ChQIAhIQ7169FBkhTKG05fTj6%2B7z5hKWAgIE97dBBAEAAAAAAGS7Df0dtS4AAAAOpnltbLcz9gKNyK89dVj0uAbv4UrxiM7gS3BG%2FtQTaUM7ryQXKFY73VJEiZY8WUQt9kDWFhIK8KUvIO%2F7h5clBEVBkFQ1f2EDhWaQHKi95R6uUij3jP8ugLBDjNGntm93lVlK0omdjdpMeeOOIjWKam%2FI%2FOb3%2BU3Q1HHYu7oXk%2FHtl6eWGGm5uoDJubfykcVq0dk8pQBSqqwI9J0xhbiwfzTJIQYmmRJBWu0xvV2jROH%2F0O2WZs5CkOfBTxXtv0LaMopDjywTjpHB1lCl4WaNer2O%2FBoo%2B%2Fmww6vS%2FrJFT3g0b579h7nfAo47DSVNL1fPYflEaQv0eYkCPczEZ1qC&acctmode=0&pass_ticket=tjLioq1kV4ZlG%2FUJASTafEK3qS1%2BV8Nuu7r7qKKaK3%2FO9%2FFLVD4DFekBR2h4jETrTzBnnZcQuYJAvDJWOi75AQ%3D%3D&wx_header=0#rd
- https://eunomia.dev/